Ransomware Attacks Are on the Rise, Again: How to Protect Your Data and Stay Safe
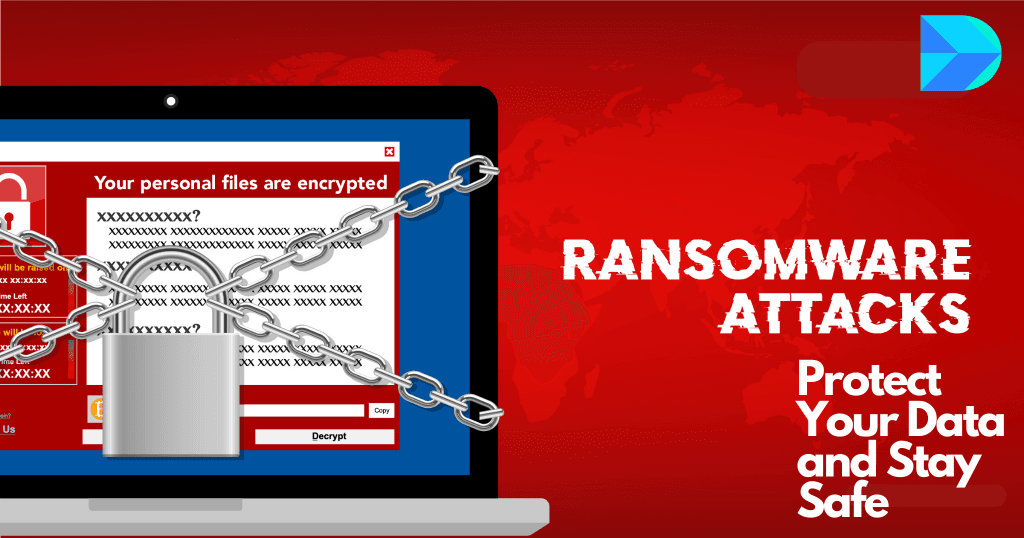
In recent times, the digital landscape has witnessed an alarming resurgence of ransomware attacks. Cybercriminals are relentless in their pursuit of exploiting vulnerabilities, making it crucial for individuals and businesses alike to fortify their cybersecurity defenses. In this blog, we’ll delve into the rising threat of ransomware attacks, understand their impact, and equip you with […]
Prompt Engineering for Effective Interaction with ChatGPT

Engineering for effective interaction with ChatGPT involves a combination of techniques to improve user experience, control output quality, and handle potential biases or harmful responses. Here are some key engineering strategies to achieve this: By employing these engineering strategies, you can enhance the interaction with ChatGPT, making it more useful, reliable, and safe for users […]
Cloud Computing Security Architecture

Cloud computing security architecture refers to the design and implementation of security measures and controls in a cloud computing environment. It encompasses various layers and components that work together to protect data, applications, and infrastructure hosted in the cloud. The architecture focuses on ensuring confidentiality, integrity, availability, and privacy of the cloud resources. Here are […]
